Unlock Remote IoT: Firewall Examples & Best Practices
Ever wondered how to access your smart devices from a coffee shop while ensuring your home network remains impenetrable? The secret lies in mastering remote IoT behind firewall examples, a critical skill in today's interconnected world.
The Internet of Things (IoT) has permeated every facet of modern life, from optimizing energy consumption in smart homes to streamlining complex industrial automation processes. The proliferation of IoT devices, however, introduces a new set of security concerns. Most organizations and individuals rely on firewalls as their primary defense mechanism against unauthorized access and cyber threats. Yet, these firewalls, while essential for security, often create barriers to seamless remote access, hindering the very functionality that makes IoT so compelling.
| Category | Information |
|---|---|
| Concept | Remote IoT behind Firewall |
| Definition | Techniques for securely accessing and managing IoT devices located behind a firewall. |
| Challenges | Firewalls block unauthorized access, hindering legitimate remote connections to IoT devices. |
| Solutions |
|
| Security Considerations |
|
| Example Scenario | Remotely monitoring and controlling industrial sensors located behind a corporate firewall. |
| Benefits |
|
| AWS IoT Registry | A service for registering and managing IoT devices within the AWS ecosystem, often used in conjunction with secure remote access solutions. |
| Further Reading | AWS IoT Platform |
- What You Need To Know About Ali C Lopez Gorlock The Destroyer
- Clallam County Jail Inmate Search Find Records More

RemoteIoT Behind Firewall Examples Unlocking Secure Connectivity

Exploring RemoteIoT Behind Firewall Examples A Comprehensive Guide
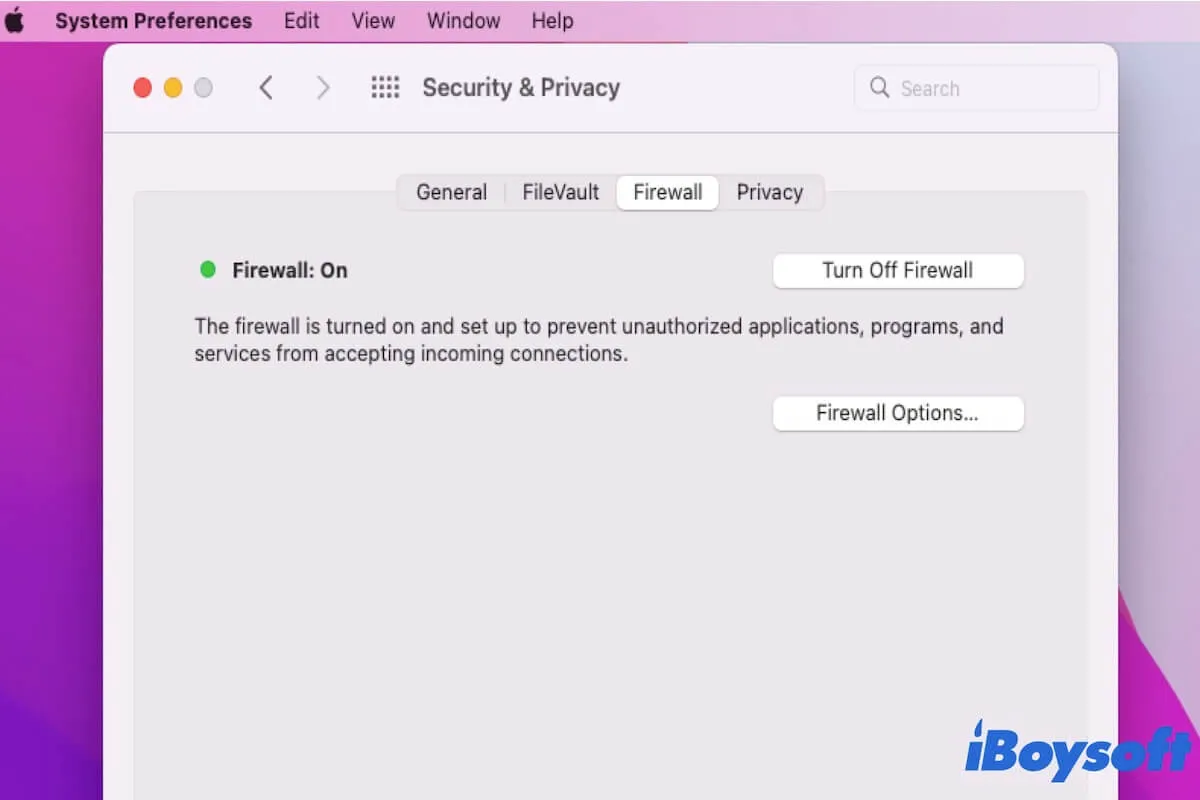
How To Use RemoteIoT Behind Firewall Using Mac The Ultimate Guide