Secure IoT: Ubuntu SSH Setup Guide For Remote Access
Are your IoT devices whispering secrets to the digital winds? Securing remote IoT devices using P2P SSH on Ubuntu isn't just a best practice; it's a necessity in today's hyper-connected world.
The proliferation of IoT devices has ushered in an era of unprecedented connectivity and convenience. However, this surge in interconnectedness has also exposed a significant vulnerability: the security of these devices. With IoT infiltrating every aspect of modern life, from smart homes to industrial automation, the imperative to protect sensitive data and maintain operational integrity has never been more critical. A compromised IoT device can serve as a gateway for malicious actors, potentially granting access to entire networks and sensitive information. The challenge lies in establishing secure, reliable connections for these devices, particularly when they are deployed in remote locations where traditional security measures may be insufficient.
| Information | |
|---|---|
| Topic | Securing Remote IoT Devices using P2P SSH on Ubuntu |
| Key Aspects | Encryption, Authentication, Secure Channel |
| Ubuntu's Role | Popular Linux distribution for IoT applications |
| SSH Benefits | Secure remote access and management |
| Configuration Steps | IP Address, DNS Settings |
| Security Measures | SSH Key Management |
| Resource | Ubuntu Landscape for IoT Management |
Ubuntu, a widely adopted Linux distribution in the IoT domain, offers a robust foundation for securing these devices. One of the most effective methods for achieving this security is through the implementation of Secure Shell (SSH), particularly utilizing peer-to-peer (P2P) connections. This approach offers a direct, encrypted communication channel between devices and a central server, bypassing the need for intermediary services that could potentially be compromised. SSH is like a digital safe house, ensuring that your communications remain private and secure. Its a key component in maintaining the integrity and confidentiality of your IoT network.
- Unveiling Susie Wiles The Republican Power Player You Need To Know
- Milan Mirabella Onlyfans Leak What You Need To Know
At its core, SSH provides several critical security features. It encrypts data to prevent interception, ensuring that sensitive information remains confidential during transmission. It authenticates users, verifying their identity and ensuring that only authorized individuals can access the devices. Furthermore, it provides a secure channel for file transfers and remote commands, allowing administrators to manage and update devices without exposing them to unnecessary risks. By implementing SSH correctly, you can encrypt the communication between your IoT devices and the control server, protecting against eavesdropping and unauthorized access.
Configuring SSH on IoT devices is a straightforward process, though it requires meticulous attention to detail. The process typically involves enabling the SSH service, generating cryptographic keys, and securing the connection through various configuration settings. One of the first steps is to configure the IP addresses and Domain Name System (DNS) settings for your Linux server and IoT devices. This ensures that they can be reliably accessed remotely. Setting up SSH on Ubuntu for IoT devices will allow you to securely access and manage your server remotely, which is crucial for setting up remote access for your IoT devices in the next steps.
A crucial aspect of securing SSH is the management of SSH keys. Managing SSH keys at scale manually is prone for human errors, key sprawls and could potentially create security loop holes. It is prudent to use an SSH key management solution to automate SSH key management. Strong key management practices are essential to prevent unauthorized access. Regular key rotation and the use of strong passphrases or key files are vital. Furthermore, it's essential to disable password authentication in favor of key-based authentication, as this significantly reduces the risk of brute-force attacks.
SSH tunneling is another powerful technique for enhancing security. It is the primary method for users to securely communicate with remote servers, networks, and devices through established firewalls and gateway routers using an assigned, protected port. It allows internet traffic to travel between local and remote devices. Port forwarding, a specific type of SSH tunneling, allows you to access services on remote machines through SSH. This can be particularly useful for accessing web interfaces or other services running on IoT devices that are behind firewalls or Network Address Translation (NAT) devices. Dynamic port forwarding involves both types of tunneling working simultaneously for inbound and outbound traffic.
Beyond basic configuration, several advanced techniques can further bolster the security of SSH connections. One such technique is to restrict access based on IP address or subnet. This limits the potential attack surface by only allowing connections from trusted networks. Another valuable practice is to regularly review and update the SSH configuration file (/etc/ssh/sshd_config). This file contains numerous settings that can be adjusted to enhance security, such as disabling root login, changing the default SSH port, and setting idle timeout values. To implement these changes, you'll need to edit the /etc/ssh/sshd_config file and restart the SSH service.
In addition to SSH, other security measures can complement its protection. Implementing a firewall on the Ubuntu server is essential to control network traffic and prevent unauthorized access. Intrusion detection systems (IDS) can also be deployed to monitor network activity and detect suspicious behavior. Furthermore, keeping the Ubuntu server and IoT devices up to date with the latest security patches is crucial for addressing known vulnerabilities. Landscape provides remote fleet management services across your entire Ubuntu estate. It allows you to manage software versions and configurations, control security patching, monitor your devices performance and compliance, access management and auditing. This blog will help you get started using Landscape to manage Ubuntu for IoT devices.
Securing remote IoT devices using P2P SSH on Ubuntu is not a one-time task but an ongoing process. Regular security audits and penetration testing are essential to identify and address potential weaknesses. Security should be integrated into every stage of the IoT device lifecycle, from design and development to deployment and maintenance. Granting remote networks access to a local server or device requires careful consideration and implementation of security best practices. Whether you're managing a fleet of IoT devices or ensuring seamless communication between peers, securing your network is paramount. Setting up a secure connection for remote IoT devices through SSH on Ubuntu server has become essential in today's interconnected world.
Connecting remote IoT devices securely using P2P SSH on an Ubuntu server is crucial in today's interconnected digital landscape. As more devices become part of the Internet of Things (IoT), ensuring secure communication is vital to protect sensitive data and maintain operational integrity. Securely connecting remote IoT devices using P2P SSH on Ubuntu is essential for safeguarding sensitive data and ensuring seamless communication. This makes it an ideal choice for securing IoT devices in remote locations. It provides a secure way to access remote servers and devices, ensuring data integrity. It encrypts your data, ensuring that your communication remains private and secure. Think of it as a digital safe house where you can manage your IoT devices without worrying about hackers.
In this guide, we will walk you through the process of setting up a Linux server for remote accessing IoT devices. This guide will walk you through the necessary steps to establish a secure connection between IoT devices and an Ubuntu server using SSH. This will allow you to securely access and manage your server remotely, which is crucial for setting up remote access for your IoT devices in the next steps. By utilizing a Linux server, you can establish secure connections and ensure seamless communication with your IoT devices.
In order to access your Linux server and IoT devices remotely, you need to configure their IP addresses and Domain Name System (DNS) settings. Enabling SSH on IoT devices. Setting up SSH on IoT devices. Configuring SSH on IoT devices is a straightforward process that involves enabling the SSH service, generating keys, and securing the connection. How to remote access Ubuntu SSH server over the. How to remote access Ubuntu SSH server over the.
IoT devices are becoming an integral part of various industries, from smart homes to industrial automation. As more devices join the Internet of Things (IoT), ensuring secure communication between them becomes paramount. Connecting remote IoT devices securely is a critical task in today's interconnected world. Execute the following command to establish a secure SSH tunnel to your IoT device's VNC server:
- Gracie Mae Thompson Scam What You Need To Know Stay Safe
- Roberto Esquivel Cabrera Worlds Longest Penis Is It A Curse

ASUS IoT and Canonical partner on Ubuntu Certification for IoT
IIOT Remote access platform for IoT devices High Peak Software
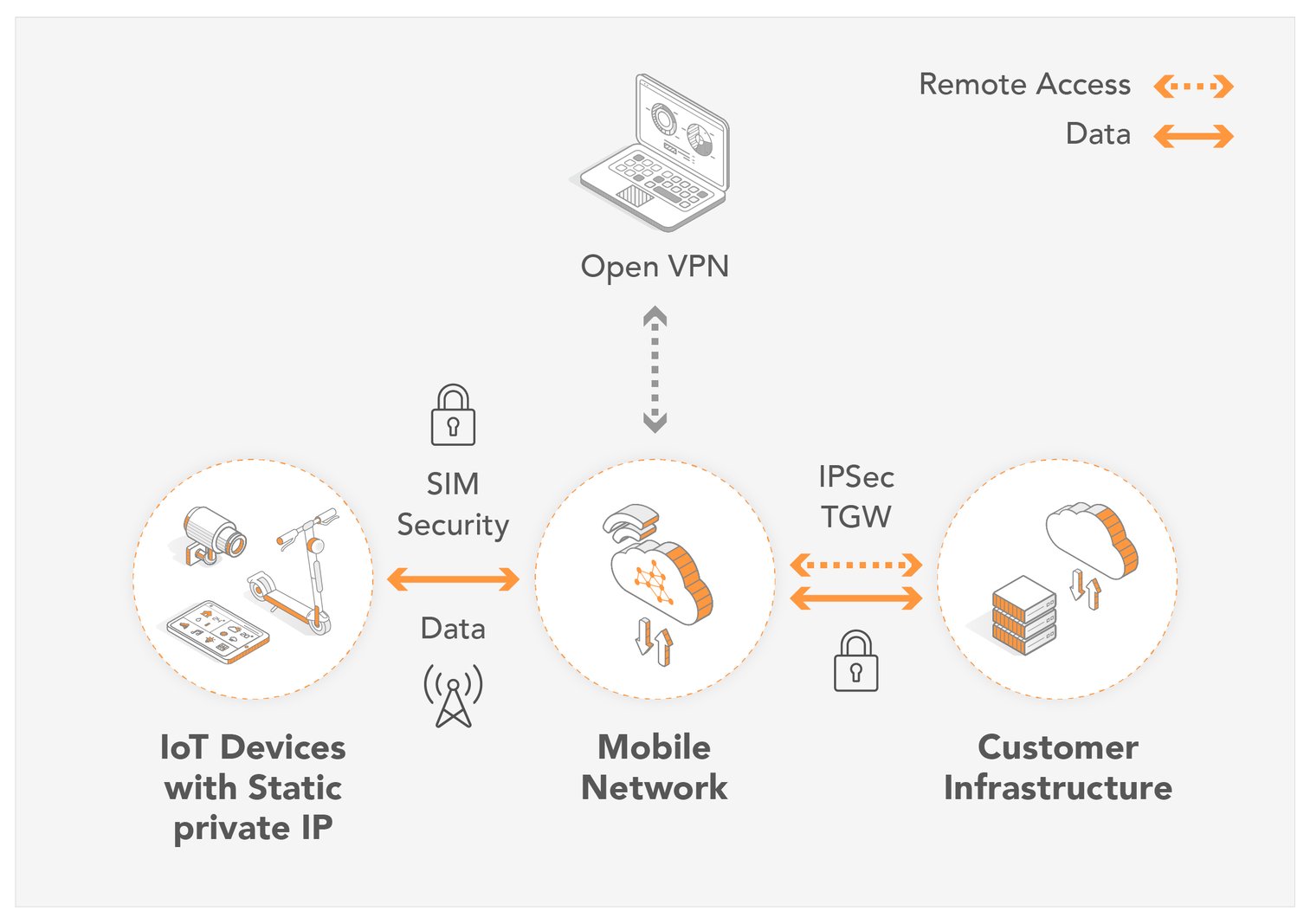
How remote device access helps IoT businesses emnify Blog